http://bit.ly/2La2FGZ
July 13, 2018 at 08:51AM
Cisco Talos
In what appears to be a case of highly-focused social engineering against a small group of iPhone users, malicious actors managed to get 13 iPhones registered on their rogue mobile device management (MDM) servers and then pushed out applications that allowed the hackers to track the locations of the phones and read victims' SMS messages.
The attacks, reported by Cisco's Talos, used the "BOptions" sideloading technique to modify versions of legitimate applications, including WhatsApp and Telegram. The initiative inserted additional libraries into the application packages, and the modified applications were then deployed to the 13 victim iPhones via the rogue mobile device management systems.
"The malicious code inserted into these apps is capable of collecting and exfiltrating information from the device, such as the phone number, serial number, location, contacts, user's photos, SMS, and Telegram and WhatsApp chat messages," wrote Talos researchers Warren Mercer, Paul Rascagneres, and Andrew Williams in a post on the attack. "Such information can be used to manipulate a victim or even use it for blackmail or bribery."
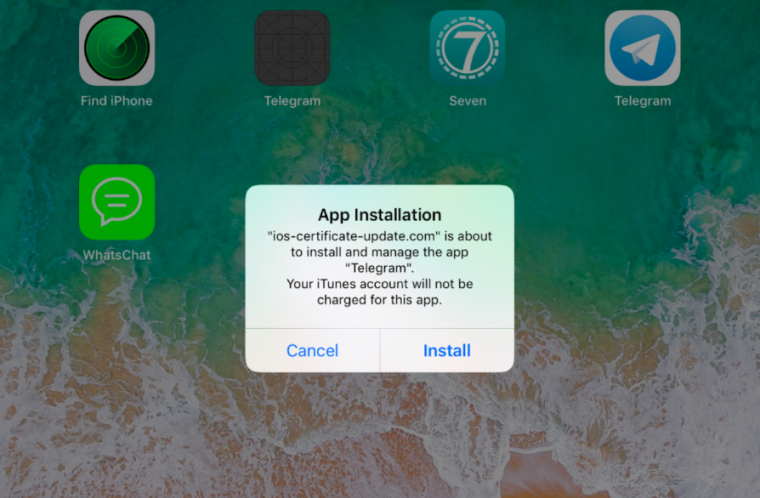
Two different MDM servers—one at the domain ios-certificate-update.com and the other at wpitcher.com—were used in the targeted attack. Both appear to have been based on the open-source mdm-server project, an Apache-licensed MDM platform. Registration with the servers—which used certificates tied to mail.ru e-mail addresses—gave the attackers essentially free rein to track the devices taken over and push malware to them. But because of the nature of MDM, successful takeover of devices would have required a substantial amount of social engineering to get users to go through all the steps voluntarily. Installation of the modified applications would have thrown up alerts to the user, as shown in the image above this article.
Talos analysts' inspection of the server found that the attackers had left information about an iPhone used as a test platform for the attack on the servers—both showed registration of a device with the same phone number, with the device names "Test" and "mdmdev." The device data showed that the attackers were likely based in India.
via Ars Technica