April 24, 2018 at 12:04PM
via Ars Technica

Amazon lost control of some of its widely used cloud services for two hours on Tuesday morning when hackers exploited a known Internet-protocol weakness that allowed them to redirect traffic to rogue destinations. The attackers appeared to use one server masquerading as cryptocurrency website MyEtherWallet.com to steal digital coins from unwitting end users. They may have targeted other customers of Amazon's Route 53 service as well.
The incident, which started around 6am California time, hijacked roughly 1,300 IP addresses, Oracle-owned Internet Intelligence said on Twitter. The malicious redirection was caused by fraudulent routes that were announced by Columbus, Ohio-based eNet, a large Internet service provider that is referred to as autonomous system 10297. Once in place, the eNet announcement caused some of its peers to send traffic over the same unauthorized routes. Amazon and eNet officials didn't immediately respond to a request to comment.
The highly suspicious event is the latest to involve border gateway protocol, the technical specification that network operators use to exchange large chunks of Internet traffic. Despite it's crucial function in directing wholesale amounts of data, BGP still largely relies on the Internet-equivalent of word of mouth from participants who are presumed to be trustworthy.
In 2013, malicious hackers repeatedly hijacked massive chucks of Internet traffic in what was likely a test run. On two occasions last year, traffic to and from major US companies was suspiciously and intentionally routed through Russian service providers. Traffic for Visa, MasterCard and Symantec—among others—was rerouted in the first incident in April while Google, Facebook, Apple, and Microsoft traffic was affected in a separate BGP event about eight months later.
Tuesday's event may also have ties to Russia, because MyEtherWallet traffic was redirected to a server in that country, security researcher Kevin Beaumont said in blog post. The redirection came by rerouting domain name system traffic and using a server hosted by Chicago-based Equinix to perform a man-in-the-middle attack. MyEtherWallet officials said the hijacking was used to send end users to a phishing site. Participants in this cryptocurrency forum appear to discuss the scam site.
The attackers managed to steal only a small amount of currency from MyEtherWallet users, most likely because the phishing site used a fake HTTPS certificate that would have required end-users to click through a browser warning. Still, Beaumont reported, the attacker wallets already contained about $27 million in digital coins, an indication the people responsible for the attack had significant resources prior to carrying out Tuesday's hack.
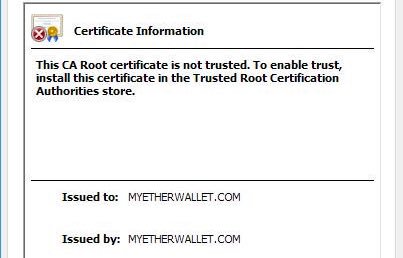
The small return, when compared to the resources and difficulty of carrying out the attack, is leading to speculation that MyEtherWallet wasn't the only target.
"Mounting an attack of this scale requires access to BGP routers are major ISPs and real computing resource to deal with so much DNS traffic," Beaumont wrote. "It seems unlikely MyEtherWallet.com was the only target, when they had such levels of access."
Another theory is that Tuesday's hijacking was yet another test run. Whatever the cause, it's a significant development because anyone who can hijack Amazon cloud traffic has the ability to carry out all kinds of nefarious actions. This post will be updated as more information becomes available.