https://tcrn.ch/2L5Frlg
July 11, 2018 at 10:21AM
You never quite know what you’ll find on the dark web. In June, a threat intelligence team known as Insikt Group at security research firm Recorded Future discovered the sale of sensitive U.S. military information in the course of monitoring criminal activity on dark web marketplaces.
Insikt explains that an English-speaking hacker purported to have documentation on the MQ-9 Reaper unmanned aerial vehicle. Remarkably, the hacker appears to have been selling the goods for “$150 or $200.”
According to Insikt Group, the documents were not classified but also contained sensitive materials, including “the M1 Abrams maintenance manual, a tank platoon training course, a crew survival course, and documentation on improvised explosive device (IED) mitigation tactics.” Insikt notes that the other set of documents appears to have been stolen from a U.S. Army official or from the Pentagon, but the source was not confirmed.
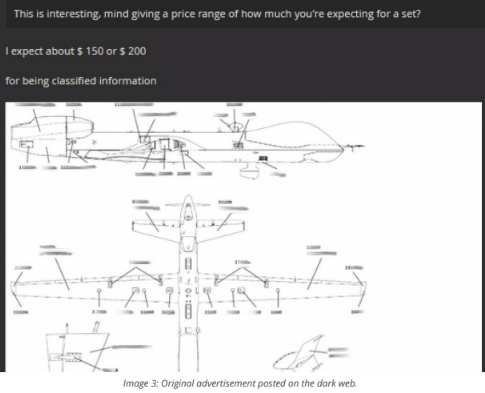
The hacker appeared to have joined the forum explicitly for the sale of these documents and acknowledged one other incident of military documents obtained from an unaware officer. In the course of its investigation, Insikt Group determined that the hacker obtained the documents by accessing a Netgear router with misconfigured FTP login credentials. When the team corresponded with the hacker to confirm the source of hacked drone documents, the attacker disclosed that he also had access to footage from a MQ-1 Predator drone.
Here’s how he did it:
Utilizing Shodan’s popular search engine, the actors scanned large segments of the internet for high-profile misconfigured routers that use a standard port 21 to hijack all valuable documents from compromised machines.
Utilizing the above-mentioned method, the hacker first infiltrated the computer of a captain at 432d Aircraft Maintenance Squadron Reaper AMU OIC, stationed at the Creech AFB in Nevada, and stole a cache of sensitive documents, including Reaper maintenance course books and the list of airmen assigned to Reaper AMU. While such course books are not classified materials on their own, in unfriendly hands, they could provide an adversary the ability to assess technical capabilities and weaknesses in one of the most technologically advanced aircrafts.
Insikt Group notes that it is “incredibly rare” for hackers to sell military secrets on open marketplaces. “The fact that a single hacker with moderate technical skills was able to identify several vulnerable military targets and exfiltrate highly sensitive information in a week’s time is a disturbing preview of what a more determined and organized group with superior technical and financial resources could achieve,” the group warns.